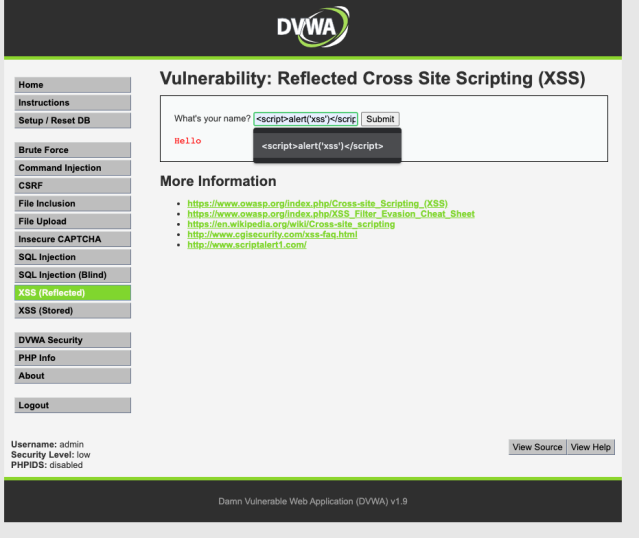
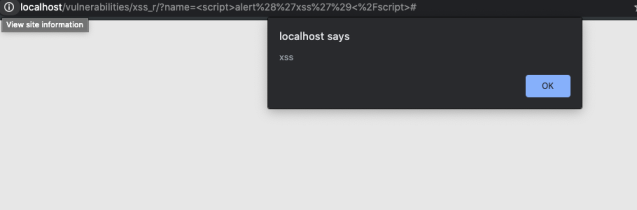
Log in as your normal user in the Juice Shop application and submit a review to one of the products.

Once the product review has been submitted click the edit review button that pops up as shown below.

Make sure your Burpsuite proxy is on and running to capture the PATCH request for our review edit. But first what is a PATCH request.
A PATCH request is a HTTP method to update partial resources on a web application. When we consider the Juice Shop and many of its intentionally vulnerable API implementations we can use the ID parameter from one users review and place it inside the other and PATCH the request and intentionally forge information displayed on the web application.
http://restcookbook.com/HTTP%20Methods/patch/
So we have captured the request and now send it to repeater in Burpsuite seen below.

Examining the id parameter we can assume that this token be repeated and submitted as though it is another user. Firstly we need to locate the id token of bender to be able to spoof and change his comments. So we will capture the thumbs up on his review and then use his id token below to change his comment on the review section. Changing the id parameter of the PATCH request captured by Burpsuite from yours to Benders id token.


Press [ Send ] and view the FireFox browser for the new comment you sent through the PATCH request Burpsuite and Juice Shop API.

Thanks for reading and happy hacking.