Today I would like to go over a couple examples of the most basic cross-site scripting attacks. Cross-site scripting attacks or XSS for short have been on the rise over the last few years. XSS is a web application based vulnerability that affects the user or client of a server or application. Typically it can be used as a leverage point to steal cookies and user authentication.
Seen initially as a very primitive attack that had affected the majority of the internet it has now come to public knowledge as a more severe attack wherein a malicious actor can wiggle their way deeper into a server or system.
Let’s get our hands a bit dirty. You will want to spin up a virtual machine with DVWA in any of your favorite VM environments or set up Docker on your local machine and import the newest version of DWVA via the terminal. I will not go over the steps here to do that, maybe at a later point, I will give a quick tutorial on how but for now let’s assume you know that part of the process.
Once you have DVWA installed and you have navigated to your localhost:port for the install on your browser we will put in our username and password and begin the exploitation process. Be sure to set the security level to low.
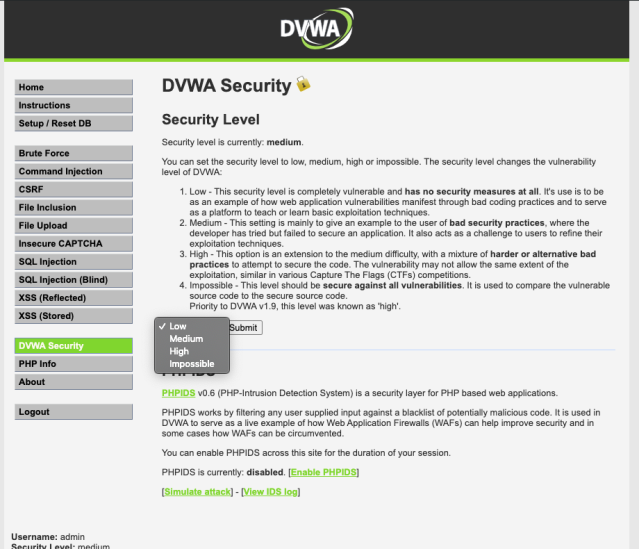
Once you have found the proper location of the DVWA security level form we will browse over to our XSS (Reflected) page to begin our exploitation process.
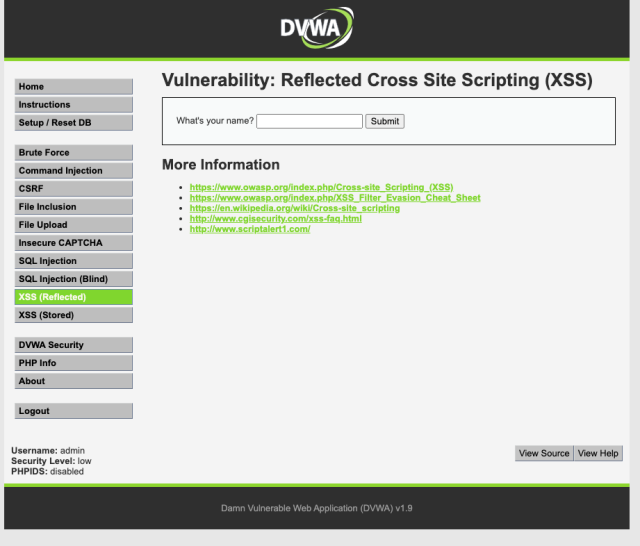
The first thing I would like you to do is place your name into the form field and hit enter. Pay attention to two things. One look at the URL above and two the location of your name on the screen.
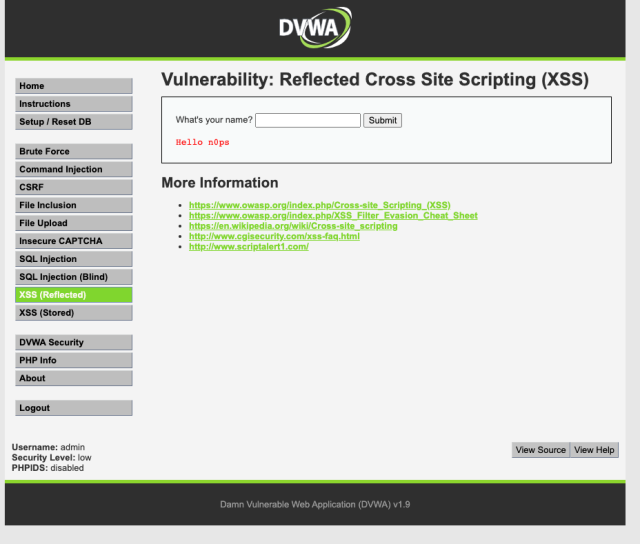

Both of these are going to be paramount to finding a successful attack. What we are looking for here is user data that can be input into a form field that will acknowledge whatever we feed into it.
Now what we are going to do is manipulate the data below to find a possible point of entry for our XSS attack. Write your name again and give it a bit of HTML text styling.
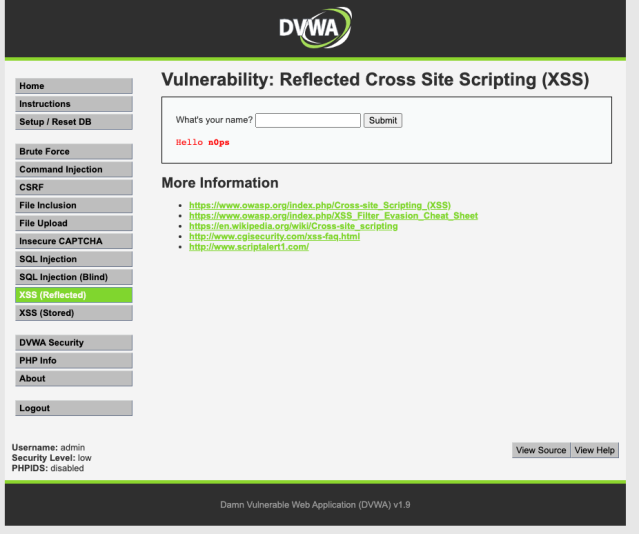

We see that as a user we can manipulate some data we place into a submit form. So lets now do our “primitive attack” on the web application. Type in the tag below and you should get a window to pop-up notifying the attacker of a flaw in the application.

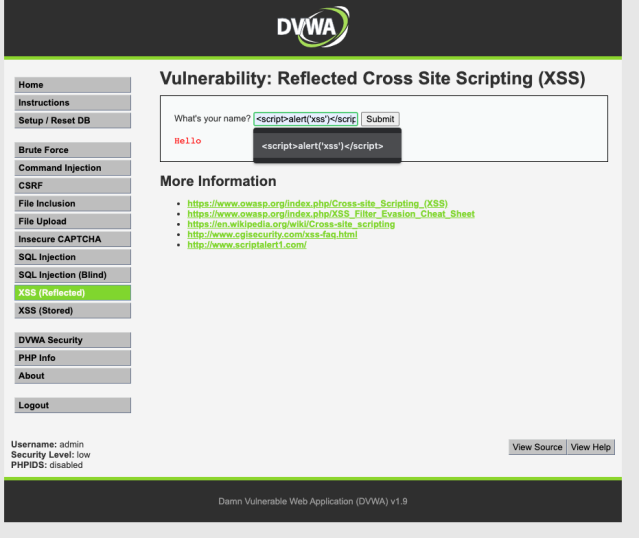
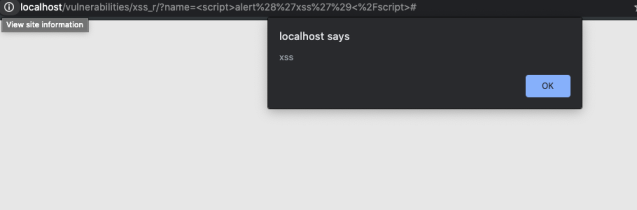
We always want to refer to the URL and the submit form. This is where we will be able to glean deeper information into the program’s function. Stay tuned for the next post on harden security measures and other ways to bypass the security of the application for finding reflected XSS.
Further reading and considerations:
Take some time to read about HTML forms, HTML and Javascript basics. Read about tags: script, iframe, img, svg. Lastly read about Javascript and HTML filters. All of this information will be paramount to you understanding how to find and locate XSS attacks in the wild.